Environment
NetIQ Identity Manager Driver - Traditional NDS / eDirectory to NDS / eDirectory Driver
Situation
NDS certificate wizard is erroring out when trying to create the certificates to secure the channel on a an Traditional eDirectory to eDirectory driver.
Is there another way to secure the channel on an eDirectory to eDirectory driver?
This procedure is not for the Bi-directional eDirectory Driver.
Is there another way to secure the channel on an eDirectory to eDirectory driver?
This procedure is not for the Bi-directional eDirectory Driver.
Resolution
Using Java SSL (JSSE) with the DirXML eDirectory Driver.
Setting up the Traditional eDir to eDir driver to use JSSE consists of two steps:
Appendix A
Add your Tree CA's Self-Signed Certificate to a Java keystore file
Setting up the Traditional eDir to eDir driver to use JSSE consists of two steps:
1. Create a server certificate in a Java keystore file.
2. Set up the Remote Loader connection parameters string on the DirXML Engine side so that the keystore file is used rather than a KMO.
The tasks are presented in detail below.
Note that task 1 as detailed below assumes that your organizational policy regarding use of certificates requires you to use certificates does not require you to use certificates generated by NPKI or some other organizational certificate authority. If this is not the case, see Appendix A for details on how to create a server certificate in a Java keystore file using an NPKI generated certificate.
The tools used to complete the tasks are the Java keytool program and Novellâs iManager. You can obtain keytool either by downloading the Java JRE or by using the JRE that is installed by eDirectory.
For more information on keytool see http://docs.oracle.com/javase/7/docs/technotes/tools/solaris/keytool.html
Note that task 1 as detailed below assumes that your organizational policy regarding use of certificates requires you to use certificates does not require you to use certificates generated by NPKI or some other organizational certificate authority. If this is not the case, see Appendix A for details on how to create a server certificate in a Java keystore file using an NPKI generated certificate.
The tools used to complete the tasks are the Java keytool program and Novellâs iManager. You can obtain keytool either by downloading the Java JRE or by using the JRE that is installed by eDirectory.
For more information on keytool see http://docs.oracle.com/javase/7/docs/technotes/tools/solaris/keytool.html
Tasks
1. Create a server certificate in a Java keystore file
1. Create a server certificate in a Java keystore file
a. Generate a key pair in the keystore:2. Set up the eDirectory Driver Parameters to use the keystore file instead of a KMO
i. keytool âgenkey âalias dirxml_key âkeyalg RSA âkeysize 2048 âdname âcn=dirxmlâ âkeypass <password> -keystore <filename> -storepass <password>b. Create a Self Signed certificate for that key pair
example: keytool âgenkey âalias dirxml_key âkeyalg RSA âkeysize 2048 âdname âcn=dirxml â âkeypass novell âkeystore dirxml.keystore âstorepass novell
i. keytool âselfcert âalias dirxml_key âkeypass <password> -keystore <filename> -storepass <password>
example: keytool âselfcert âalias dirxml_key âkeypass novell âkeystore dirxml.keystore âstorepass novell
a. For both servers in the eDirectory to eDirectory connection do the following.
i. Copy the keystore file created in task 1 (dirxml.keystore) to the dib directory on the server. (/var/opt/novell/eDirectory/data/dib by default)
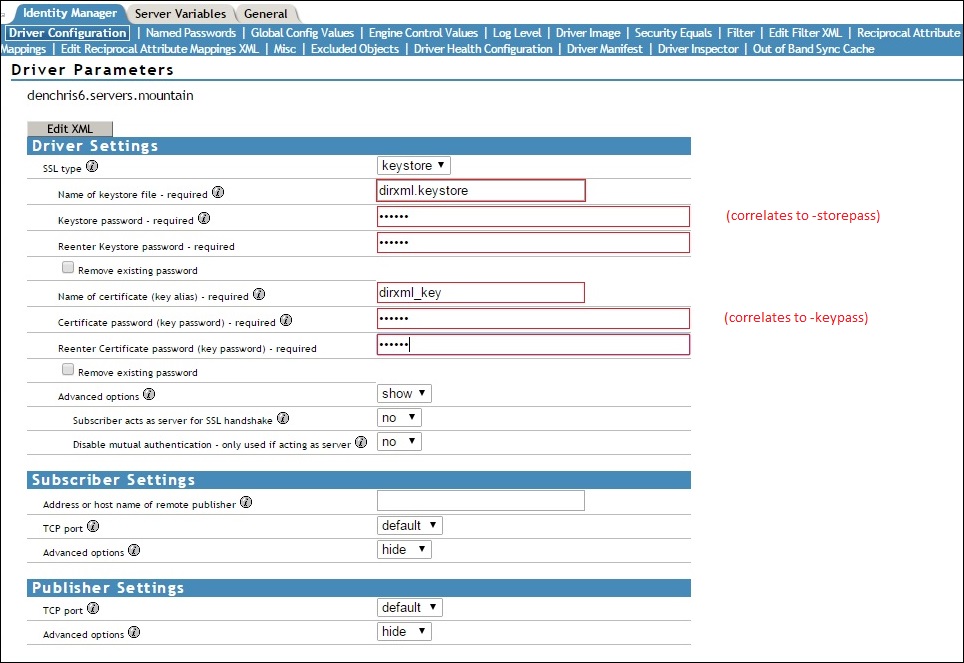
ii. Edit the properties of the Traditional eDirectory driver (iManager, Identity Manager Role, Driver Set Overview Task, search for and select your driver set, Edit Properties of your eDirectory driver). On the Driver Configuration tab, scroll down to Driver Properties.
Select the SSL Type as Keystore, Fill in the keystore file name you placed in the dib directory, keystore password, Name of the certificate (alias) and certificate password. Advanced options shown are defaults of no.
Note: If your driver is missing the SSL type selection under the Driver Settings, then you are running an OLD Version of the the driver. Likely created with an old eDir driver configuration file prior to IDM 4.x. It is recommended you install a new version of the driver using the current driver packages with Designer for IDM 4.x or later which will have the shown Driver Settings in it. If you do not want to do so, then you can copy the driver parameters from a test eDir driver you create and paste them in your eDir Parameters. (always export / backup your driver prior to making changes on a working driver)
iii. On the properties of the eDirectory driver, clear the Authentication ID field (where the KMO name would normally go). Make sure it is blank (no spaces or anything), or your driver will not start.
iv. Save the changes and restart the driver
Appendix A
Add your Tree CA's Self-Signed Certificate to a Java keystore file
a. Export the self-signed certificate from your treeâs Certificate Authority in base-64 format.i. In iManager, select the eDirectory Administration/Modify Object task.
ii. Browse to your treeâs Certificate Authority. Click OK.b. Import your treeâs self signed certificate into a new keystore file:
iii. Click on the Certificates tab.
iv. Click on Self Signed Certificate
v. Click on the Export button.
vi. Uncheck the box to "Export private key", Select BASE64 as the Export format, then click Next.
vii. Click on Save the exported certificate, and save the file.
i. keytool âimport âfile <name of cert file> -trustcacerts ânoprompt âkeystore <filename> -storepass <password>.c. Generate a key pair in the keystore:
example: keytool âimport âfile cert.b64 âtrustcacerts ânoprompt âkeystore dirxml.keystore âstorepass novell
i. keytool âgenkey âalias dirxml_key âkeyalg RSA âkeysize 2048 âdname "<dn name>â âkeypass <password> -keystore <filename> -storepass <password>d. Continue on with Step 2 above, Set up the eDirectory Driver Parameters to use the keystore file instead of a KMO
example: keytool âgenkey âalias dirxml_key âkeyalg RSA âkeysize 2048 âdname âcn=dirxmlâ âkeypass novell âkeystore dirxml.keystore âstorepass novell