Environment
Self Service Password Reset 3.3.1.x
Self Service Password Reset 4.x
LDAP Directory
Situation
Need to restrict user access to SSPR based on users' group membership.
Resolution
This can be setup by making a change in the SSPR Configuration Editor and modifying your LDAP Profile(s).
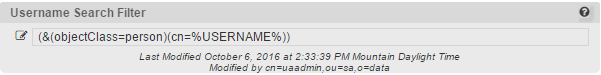
In your Configuration Editor, go to LDAP > LDAP Directories > {select your profile, often "default"}. From here you need to look for "Username Search Filter."
Above is the default parameter that is set in SSPR at installation. You'll want to replace it with the following, depending on eDirectory or Active Directory:
eDirectory
(&(objectClass=person)(cn=%USERNAME%)(groupMembership={full group context here}))
Example - (&(objectClass=person)(cn=%USERNAME%)(groupMembership=cn=ssprAccess,ou=groups,o=data))
Active Directory
(&(objectClass=person)(sAMAccountName=%USERNAME%)(memberOf={full group context here}))
Example - (&(objectClass=person)(sAMAccountName=%USERNAME%)(memberOf=CN=ssprADAccess,CN=Users,DC=chansen7,DC=lab,DC=novell,DC=com))
In each case, it is looking for the username that is entered at login, and then verifying that it's a part of the group specified in the filter.
Please note - If you have changed the LDAP Naming Attribute under the LDAP Profile settings to be anything other than cn for eDirectory, or sAMAccountName for Active Directory, then you need to change them in the above example filters respectively.
Additional Information
It is also worth mentioning that if a user happens to know their full LDAP context, then they can login to SSPR regardless of the above settings.
If, for example, I logged in with a username of cn=test,ou=sa,o=data, and then entered in a password, it will ignore the above settings because they are specific to contextless login, and still proceed to log the user in.