Environment
Reflection for Secure IT Windows Server version 7.0 or higher
Reflection for Secure IT UNIX Client version 7.0 or higher
Reflection for Secure IT UNIX Server version 7.0 or higher
Situation
Resolution
Data Encryption with Ciphers
Encryption is used to protect the security of data in transit. Data is encrypted with a cipher (algorithm) before it is sent and decrypted using the same cipher once the transmission is received.
There are multiple types of ciphers supported by ssh clients and servers. Once you decide which cipher types you want to permit in your environment, configure the ssh server to enforce the use of those cipher types. Then, configure the ssh clients in your environment to use one or all of those cipher types.
The list of available ciphers on the server control what cipher types can be used; however, if there are multiple cipher types to choose from, it is the ssh client that determines which cipher type is actually used for the connection. When the ssh client attempts to initiate a connection to the server, during the key exchange the client presents its list of supported cipher types to the server, in order of preference. The cipher used for that session is the first cipher type on the list presented that is also supported by the server.
Reflection for Secure IT supports the following cipher types:
| Cipher Type | Values | Supported in Reflection for Secure IT Windows Versions | Supported in Reflection for Secure IT UNIX Versions |
| AES Counter Mode | aes128-ctr aes192-ctr aes256-ctr | 7.1 or higher | 7.0 SP1 or higher |
| AES CBC Mode (also known as Rijndael) | aes128-cbc aes192-cbc aes256-cbc | 7.0 or higher | 7.0 or higher |
| TripleDES | 3des-cbc | 7.0 or higher | 7.0 or higher |
| Cast (128-bit) | cast128-cbc | 7.0 or higher | 7.0 or higher |
| Blowfish (128-bit) | blowfish-cbc | 7.0 or higher | 7.0 or higher |
| Arcfour128/256 | arcfour256 arcfour128 | 7.1 or higher | 7.0 or higher |
| Arcfour | arcfour | 7.0 or higher | 7.0 or higher |
Configuring the Reflection for Secure IT Windows Server
Follow these steps to configure the server cipher types.
- Start the Reflection for Secure IT Windows Server configuration console.
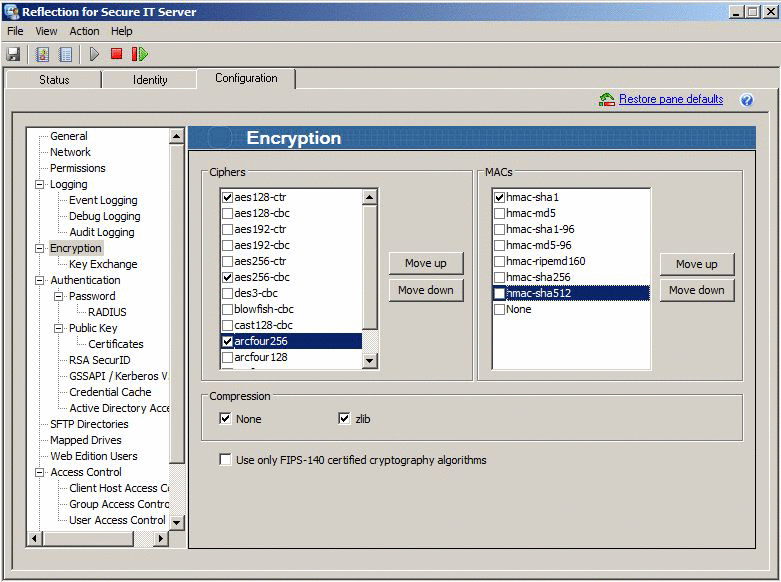
- On the Configuration tab, click Encryption.
- In the Ciphers list, select the cipher type(s) you want to use. Or, you can select the "Use only FIPS-140 certified cryptography algorithms," and Reflection pre-selects just FIPS-140 certified ciphers and MACs.
Note: Using the Move up and Move down buttons does not set the order of precedence for cipher or MAC usage. The order of precedence is determined by the client.
- Click File > Save Settings.
Configuring the Reflection for Secure IT Windows Client
Follow these steps to configure the client cipher types.
- Start Reflection for Secure IT Windows Client.
- Click Connection > Connection Setup.
- Enter your Host name and User name, and then click Security.
- On the Encryption tab, in the Cipher List, all cipher types are selected by default. Clear the check boxes for the cipher type(s) you do not want to use for this connection.
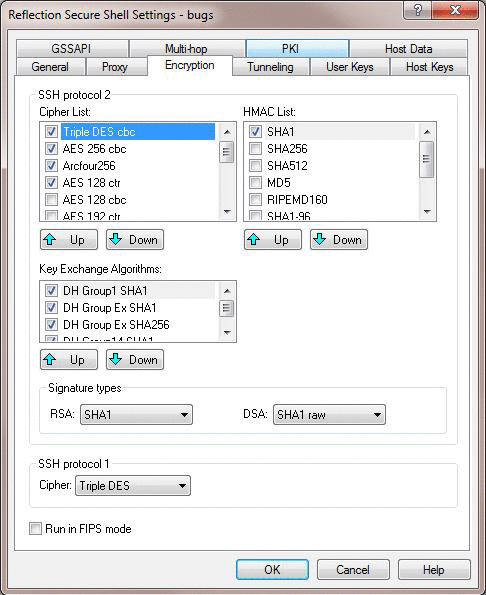 Figure 2: Client Configured for Triple DES cbc, AES 256 cbc, Arcfour256, and AES 128 ctr
Figure 2: Client Configured for Triple DES cbc, AES 256 cbc, Arcfour256, and AES 128 ctr- Once only the cipher type(s) you want to enable are selected, use the Up and Down buttons to rank them in order of preference from top (first) to bottom (last).
When negotiating a server connection, the client starts with the first cipher type on this list and checks to see if the server supports it. If does not, the client moves on to the next cipher on the list, until a mutually supported cipher type is found.
If you were using the server shown in Figure 1 and the client shown in Figure 2, the first mutually supported cipher type is AES 256 cbc.
Alternately, if you select "Run in FIPS mode, " Reflection pre-selects just FIPS-140 certified ciphers and MACs.
- Click OK. This action saves any changes made to the default list of cipher and HMAC lists to the userâs config file.
- Click Connect.
- Click File > Save to save the connection with your security settings.
Configuring the Reflection or Secure IT UNIX Server and Client
The UNIX client and server use the ssh2_config and sshd2_config configuration files to support the same keywords for configuring ciphers as those used by the Windows client and server.
When negotiating a server connection, the client starts with the first cipher type listed in the ssh_config file and checks to see if the server supports it. If it does not, the client moves on to the next cipher on the list, until a mutually supported cipher type is found.
For example, in the sample config file entries shown below, the first mutually supported cipher type is aes256-cbc.
For further information on Cipher keywords, refer to your UNIX server's sshd2_config and ssh2_config man pages.
For information about Reflection for Secure IT UNIX Server and Client, see the Reflection for Secure IT UNIX User Guide at https://docs.attachmate.com/reflection/rsit-ssh/8.0/unix/en/help/.
Configure the UNIX Server
Configure server keywords in the /etc/ssh2/sshd2_config file.
For example, to configure the UNIX server for aes128-cbc, aes192-cbc, and 3dec-cbc, edit the sshd2_conf file to include the following comma delimited Ciphers entry.
Ciphers aes128-ctr,aes256-cbc,arcfour256Configure the UNIX Client
Configure client keywords in the global /etc/ssh2/ssh2_config file. These settings apply to all client connections.
For example, to configure the UNIX client for aes128-cbc, aes192-cbc, and 3dec-cbc, edit the ssh2_conf file to include the following comma delimited Ciphers entry.
Ciphers 3des-cbc,aes256-cbc,arcfour256,aes128-ctrNote: In this example, the first mutually supported cipher type is aes256-cbc.
Additional Information
Legacy KB ID
This document was originally published as Attachmate Technical Note 2401.